Internet security is one of the most important aspects when it comes to the world wide web. There has been constant research and development to improve the security of applications and files on the Internet and thus to prevent malicious use.
Downloadable files over the Internet are often the target of attacks on the Internet. As thousands and thousands of people download these files regularly, it becomes especially important to protect such files.
In this article, we will learn about checksums and how they can be used to authenticate a downloaded file from the Internet.
What is a SHA256 Checksum?
A Checksum is a cryptographic signature of a file. It is basically a string that uniquely represents the file; thus if a file is ‘tampered‘ with or ‘modified‘, its checksum value will change and the user will know that the file has been changed.
There are a number of mathematical algorithms for generating Checksum for a file in Linux. One such algorithm which is very popularly used is SHA256, which stands for ‘Secure Hash Algorithm 256‘ and was developed by the United States National Security Agency.
This algorithm breaks down the data of the file into small-sized parts and creates and combines the hash values for each part to create the checksum value. The SHA256 Checksum is usually provided in a text file or directly as a string along with the main file, in its download section on the Internet.
Verifying SHA256 Checksum of a File in Linux
Let’s take an example of Ubuntu Groovy (20.10) ISO file download and try to verify its checksum. Note that along with the ISO files, the text file ‘SHA256SUMS‘ is provided which contains the checksum values.
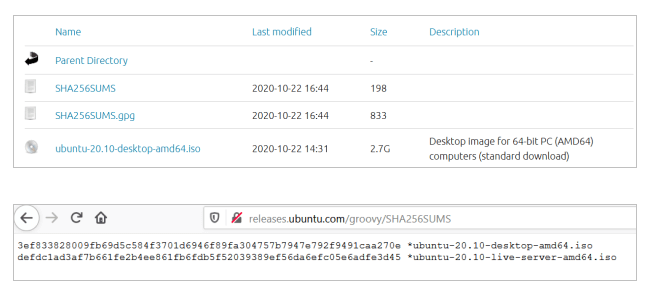
Download the ISO file for Ubuntu 20.10 desktop and the file SHA256SUMS in the same folder and go to the folder where they are downloaded.
$ wget http://releases.ubuntu.com/groovy/ubuntu-20.10-desktop-amd64.iso $ wget http://releases.ubuntu.com/groovy/SHA256SUMS $ cd ~/Downloads
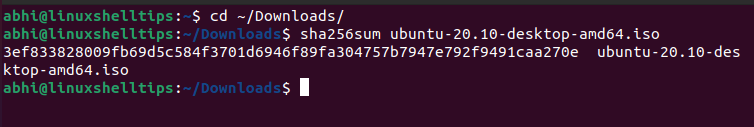
To generate a checksum of the ISO file, run the following:
$ sha256sum ubuntu-20.10-desktop-amd64.iso
To compare the checksum to the value in the file SHA256SUMS, run the command with the '-c' flag. This will take all the checksums in the file, compare them with the corresponding filename, and print the filename that matches the checksum.
$ sha256sum -c SHA256SUMS
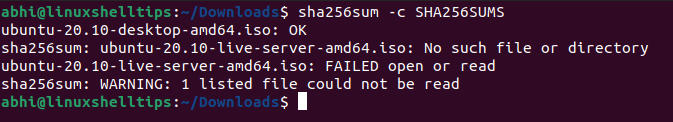
As seen above, the ISO file matches the original checksum, and hence we can be sure that the file was not modified or tampered with in any way during the download.
The other output is regarding the 2nd checksum in the file: for the live server ISO file which is not downloaded and hence the command prints those errors.
Conclusion
Today we learned how to verify the sha256 checksum of a file in Linux. Make sure you check out the manual page of sha256sum (by running ‘man sha256sum‘) to learn more in-depth about the command.
$ man sha256sum
Thanks for reading and let us know your thoughts or questions in the comments below!

Where is the information on how to run sha256sum?
I get:
Thanks
@Markus,
You need to install coreutils package on your Linux distribution.
Can the command be run against an optical disk or usb disk instead of an iso file? How does one indicate the device (e.g. sdb1)?
@Charles,
The command sha256sum only check the checksum of the file, not a device or disk…
On Linux disks are files. (e.g. /dev/sdX) it should work. The place where it is problematic is where a compressed image is provided and then decompressed before copying to the disk.
And what if the checksum is provided in some format other than a file? for example what if they just provide some text on a web page?
@Tfj,
Then you can run the sha256sum by mentioning the hash on the command itself and compare the results with the hash on the website as shown.
In today’s Internet environment this article is timely and helps’s eliminate the complexity. Thanks!