SSH or Secure Shell is an invaluable utility when it comes to undertaking remote login objectives on remote machines. For Linux users, the SSH utility offers more than just remote login solutions.
The mentioned users are also able to effortlessly accomplish Linux administrative tasks. Regardless of whether the targeted remote machine is untrustworthy or whether the network that facilitates the communication between the two machines is insecure, SSH ensures that these communications are secure and encrypted.
It is sometimes frustrating when an SSH session ends too soon while we are multitasking on the Linux terminal environment. Finding a way of keeping the SSH session alive for as long as possible can be a game changer for Linux users who don’t want to keep on re-initiating new SSH sessions.
This article will walk us through the needed steps that will help us keep any SSH session alive as long as possible until we manually decide to close the Linux terminal window.
Prerequisites
- Have openssh-client installed on the Linux system initiating the SSH connection (client machine).
- Have openssh-server installed on the remote Linux system receiving the initiated SSH connection (server machine).
Why SSH Sessions End
Usually, it is the ssh daemon running on the server machine that makes it possible for an ssh connection from the client machine to be possible. If the SSH connection is successful and the server and client machines do not periodically communicate, the server machine closes the connection after some fixed grace period.
To address this issue, we have made some configuration changes on an SSH config file on either the server or client machine.
When SSH Connection is Coming from the Client Machine
On the client machine, the SSH config file should be located at $HOME/.ssh/config. If it does not exist, we will need to create it.
$ cat $HOME/.ssh/config OR $ touch $HOME/.ssh/config
Use the chmod command to reserve the read and write privileges of this file only to the current user and no other user. In short, we are keeping this file access private.
$ chmod 600 $HOME/.ssh/config
Let us now open and add some ssh rules to this file, you can use a text editor of your choice if needed.
$ nano $HOME/.ssh/config
Add the following lines in the file before saving and closing it.
Host *
ServerAliveInterval 300
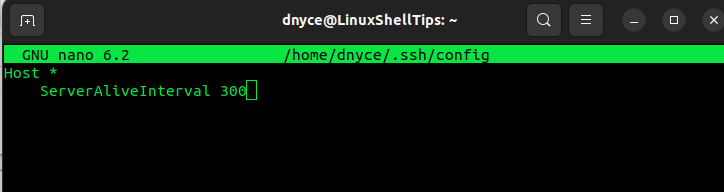
If your SSH connection is tied to a specific host, you could edit the above file entry to look like the following:
Host my_hostname.com
ServerAliveInterval 300
From the above demonstration, the client machine will wait for 300 seconds before allowing the server machine to close the ssh connection.
When SSH Connection is Coming from the Server Machine
You might also find yourself in circumstances where you need to use your server machine or a remote machine to access a client.
On the server machine, access and open the file /etc/ssh/sshd_config or /etc/ssh/ssh_config as its naming convention sometimes depends on the Linux OS distribution in use.
$ sudo nano /etc/ssh/ssh_config
Since we are after an ssh connection to a client machine, add the following key value at the bottom of the file:
ClientAliveInterval 300
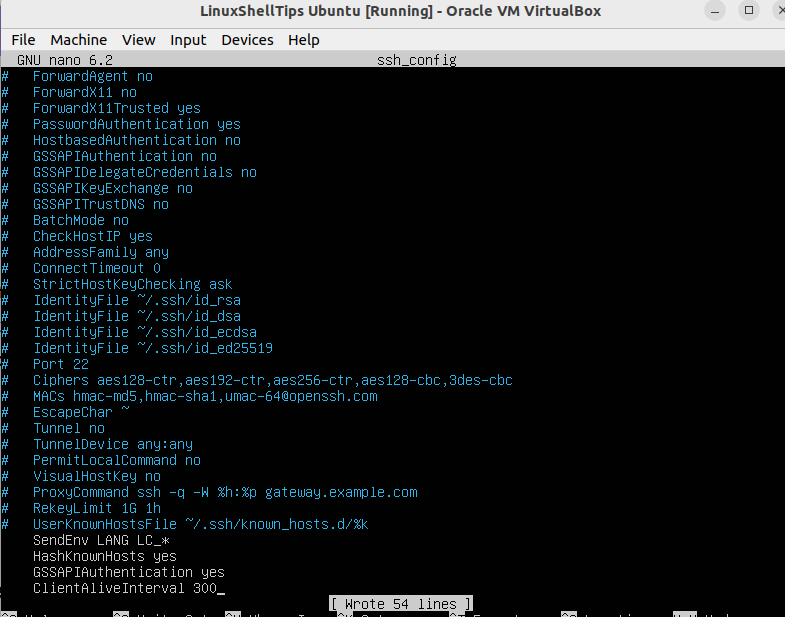
This value ensures that the SSH connection lasts for 300 seconds before the connection is timed out.
It is also advisable to set a timeout value when accessing machines from hosting platforms to avoid high run-up costs especially when their billings are per minute.
When using the client machine for ssh connection, your updated config values in the file $HOME/.ssh/config will look like this:
Host *
ServerAliveInterval 300
ServerAliveCountMax 2
When using a server machine for an ssh connection, your updated config values in the file /etc/ssh/ssh_config will look like this:
ClientAliveInterval 300 ClientAliveCountMax 2
We can now comfortably handle ssh sessions without worrying about unexpected timeouts. Hope you enjoyed the article. Feel free to leave a comment or feedback.
