While working with Linux, we find that access to some files or performing sensitive operations requires users to have elevated privileges. The sudo command temporarily elevates user privileges allowing a user to execute sensitive commands or access files without restrictions.
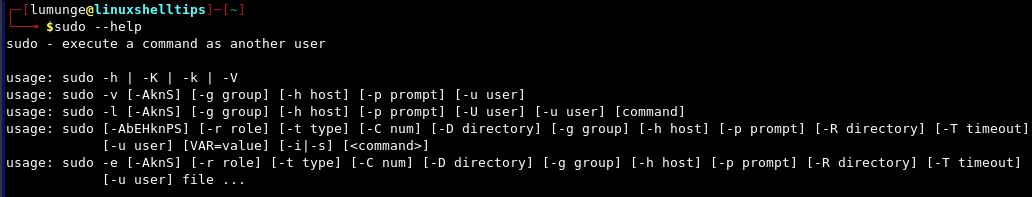
The syntax of the sudo command is as follows:
$ sudo --help
We discuss four ways in which we can execute sudo commands without having to enter a password every time. The first two involve editing the sudoers and sudoers.d files while the last two involve executing commands to elevate user privileges to root.
1. Editing the /etc/sudoers File
First, let us try to execute a command with sudo and see if we get a password prompt:
$ sudo systemctl start mariadb
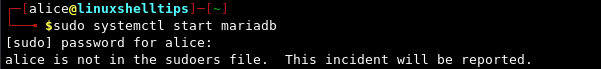
Run Sudo Commands Without Password
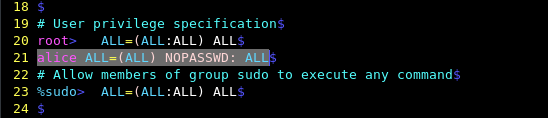
If we want user Alice to execute all sudo commands without needing a sudo password for any/all hosts, we edit the sudoers file.
$ sudo visudo
and use the NOPASSWD directive as shown:
alice ALL=(ALL) NOPASSWD: ALL
Run Particular Sudo Commands Without Password
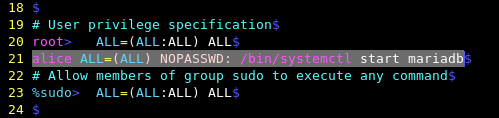
To allow user Alice to execute a single specific sudo command without entering a password, you need to use the following line to the sudoers file.
alice ALL=(ALL) NOPASSWD: /bin/systemctl start mariadb
Now try to execute a few commands and see…
$ sudo systemctl start mariadb $ sudo systemctl status mariadb $ cat /etc/sudoers
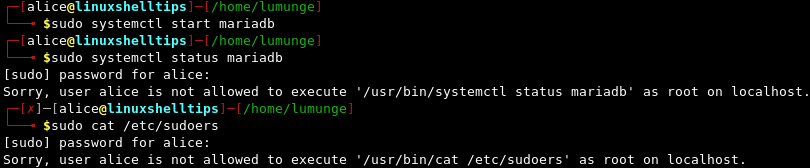
From the above terminal session, we started the MariaDB service because of the changes we made to the sudoers file, we do not have a password prompt. Also notice that for the subsequent commands, we have a password prompt.
Run Sudo Commands on Specific Host Without Password
To allow the user to execute the commands on a specific host as root, instead of using ALL we write:
alice linuxshelltips1=(root) NOPASSWD: /bin/systemctl start mariadb
The above allows Alice to execute the listed command on a host with the name linuxshelltips1 without entering a password.
To allow three commands to be executed with sudo privileges for a host linuxshelltips1 and not have a password prompt we list them as follows:
alice linuxshelltips1=(ALL) NOPASSWD: /bin/systemctl start mariadb, /bin/systemctl status mariadb, /bin/cat /etc/sudoers
Here we allow the user Alice to start and check the status of the mariadb service without entering a password while on a host with the hostname linuxshelltips1. The user can also concatenate the /etc/sudoers file without entering a password.
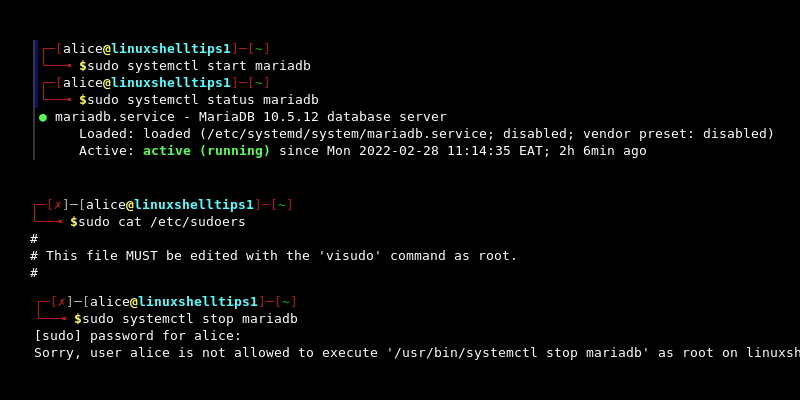
All three commands are executed without requiring a password. However, when we try to stop the mariadb service, we are prompted for a password since we did not specify it in the sudoers file.
Run Sudo Commands Without Password for Group Users
We can also allow sudo commands to run without entering a password for a group of users, say group1 to which user Alice belongs.
%group1 ALL=(ALL) NOPASSWD: ALL
We can also combine users, groups, and commands. For example, if we only want a specific user or group to execute specific commands, we paste the following line in the sudoers file:
alice,%group2 ALL=(ALL) NOPASSWD: /bin/systemctl, /bin/cat, /bin/kill
Alice and all users belonging to group2 can execute all systemctl, cat, and kill commands with sudo and not have a password prompt.
We can also allow specific users (alice, bob) to execute specific commands (systemctl, cat, kill) by listing them as follows:
bob,alice, ALL=(ALL) NOPASSWD: /bin/systemctl, /bin/cat, /bin/kill
After saving the file, alice and bob can execute systemctl, cat, and kill commands on all hosts without being prompted for a password.
Notice how we list commands in the /bin/ directory, such as; bin/systemctl, or /bin/cat. Instead, we could include the whole directory and end with a ‘/’ character. This would mean that the user can execute any command in the /bin directory. However, this does not apply to commands in subdirectories of /bin directory.
For example, to allow Alice to execute all commands in the /bin/ directory we write:
alice ALL=(ALL) NOPASSWD: /bin/
Alice can now execute all commands on all hosts that require sudo privileges located in the /bin/ directory without requiring a password.
2. Editing the /etc/sudoers.d File
Alternatively, it is safer to make changes to the /etc/sudoers.d instead of the sudoers file. This makes managing sudo privileges more manageable and leaves the sudoers’ file untouched.
Note that all we have discussed in the previous section is applicable here, the only difference is that we will be working with the sudoers.d file for safety purposes.
For example, let’s create a file for alice allowing her to execute sudo commands on a specific host without entering a password.
$ sudo nano /etc/sudoers.d/alice
After the file is open, we paste the following line:
alice linxshelltips=(root) NOPASSWD: /bin/
The user can now execute all sudo commands in the /bin/ directory without entering a password on the host with the hostname linuxshelltips.
We could also specify sudo commands that can be executed by a group of users as follows:
$ sudo nano /etc/sudoers.d/groups
We paste the following line to allow all members of the group1 to run all sudo commands on all hosts without entering a password.
%group1 ALL=(ALL) NOPASSWD: ALL
Managing sudo privileges this way allows us to easily manage them without worrying about breaking something.
3. Fixing Sudoers File
Notice how we use visudo to edit the sudoers files? This is the convention because we want to avoid breaking the system. When we run visudo it checks up on the file to make sure that we did not mess anything up for example in terms of syntax.
If instead we used a plain text editor and made mistakes, this will prevent us from editing the file again since we need sudo privileges to edit the file.
Using visudo also prevents multiple edits to the sudoers file at a time, that is, if another user is editing the file, other users will not be allowed to edit the file.
Assuming the sudoers file is messed up and we are locked out. We use the pkexec command which is an alternative to the sudo command.
$ pkexec visudo
After we have access to the sudoers file, we can fix the mistake. For example, to fix the /etc/sudoers.d/alice file, we write:
$ pkexec visudo /etc/sudoers.d/alice
4. Using ‘sudo -s’ Command
To run these commands without entering a password every time, we execute the command:
$ sudo -s
When we enter the password once, for all subsequent sudo commands in this terminal session, we do not have to enter it again.
Now, if we try to run a sudo command, we won’t be prompted to enter a password:
$ sudo systemctl start mariadb.service
We exit this mode by issuing the exit command:
$ exit
5. Using ‘sudo su’ Command
Another way to execute sudo commands without being prompted for a password is to run the sudo su command to become the root user. After this command executes, and we enter the password once, then for all subsequent sudo commands, we do not need to enter the password for them to run.
$ sudo su
Now, we have root privileges so any subsequent sudo commands we execute will not require us to enter a password.
Generally, to run sudo commands without a password, we use the following syntax while editing the sudoers.d file:
user_list host_list=effective_user_list tag_list command_list
Where,
- user_list can be specific users, groups, aliases.
- host_list is the hostnames of hosts in which a user can run sudo commands without a password.
- effective_user_list specifies the list of users running as the current user or as an alias of the current user.
- tag_list specifies tags such as NOPASSWD.
- command_list specifies a list of sudo commands that the user or group can execute without requiring a password.
Executing sudo commands without a prompt for entering the password is considered a security risk. A password prompt not only gives us a chance to confirm a command before it is executed but also prevents unauthorized users from performing actions beyond their privileges.
For example, the ‘sudo rm -rf /’ command erases the whole file system. This command is irreversible and therefore, it is wise to have a password prompt as it gives us a chance to evaluate this action.
