Unlike changing a WordPress admin user password where the needed steps are superuser-oriented, the steps needed here are system-oriented. In such circumstances, a WordPress user is usually completely unaware of their Admin user password. Also, going for the “Lost Password” option might be out of the question as to the associated WordPress Admin user email address may also be inaccessible.
In such circumstances, only a system administrator that has full control of the MySQL database daemon is in a better position to reset all the Admin passwords for all the privileged WordPress users.
As a system administrator, it will be easier to manage such password reset situations when you have a directory file and mechanism to easily generate random user passwords and encrypt them before a user is assigned one.
Generating Random User Passwords in Linux
Through MD5 Hash encryption, it is relatively easier to achieve this objective. Let us create a random file called my_generated_passwords.txt.
$ sudo touch my_generated_passwords.txt
With a random password in mind, create an MD5 Hash version encryption of it.
$ sudo echo -n "SomePa55w@d" | md5sum
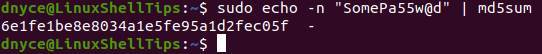
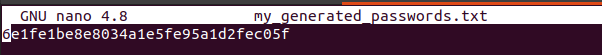
Copy this generated MD5 Hash to the file you created earlier and save it. We will use it later on in resetting a WordPress Admin user password.
$ sudo nano my_generated_passwords.txt
Resetting Your WordPress Admin Password via MySQL
It is now time to use your root-privileged system administrator credentials to log in to your MySQL/MariaDB database through the command-line interface.
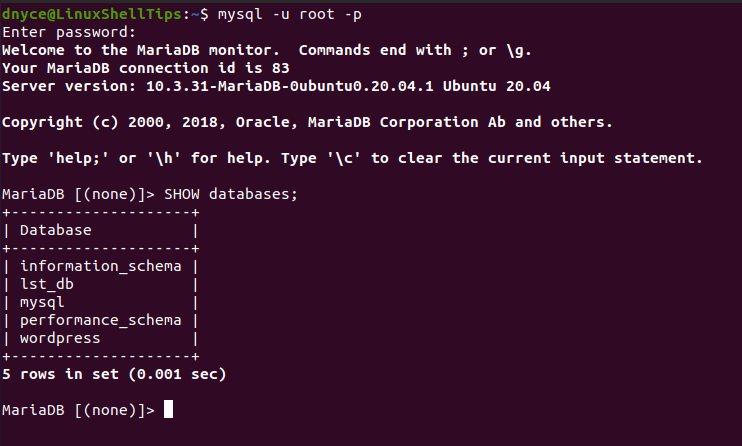
$ mysql -u root -p
Display all the existing databases.
MariaDB [(none)]> SHOW databases;
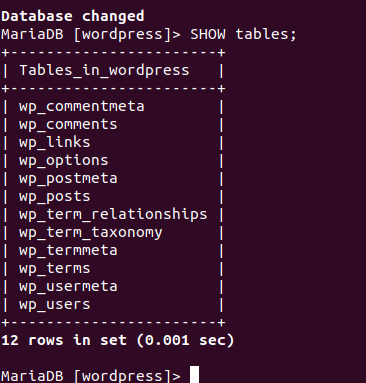
Switch to the WordPress database associated with your site users and list the associated WordPress database tables..
MariaDB [(none)]> USE wordpress; MariaDB [(none)]> SHOW tables;
The WordPress database table we are after is wp_users. It is the one that holds all the users of the site regardless of their access privilege levels.
MariaDB [(none)]> DESCRIBE wp_users;
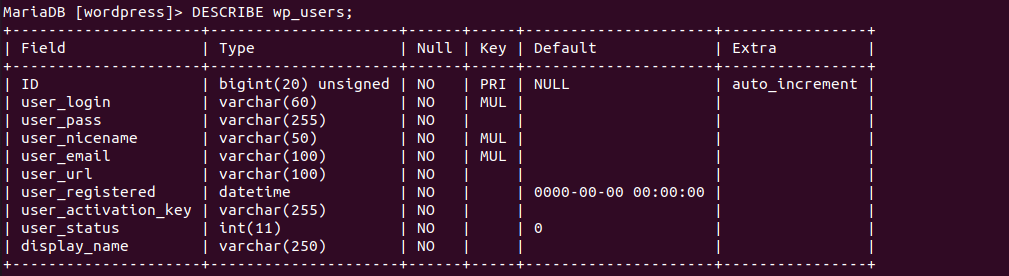
From the above description of the wp_users WordPress database table, we mostly need the user_login column value for reference and the ID column value tied to the user_login to successfully reset the targeted Admin user password.
MariaDB [(none)]> SELECT ID, user_login FROM wp_users;
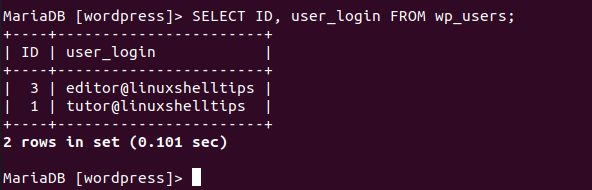
In this case, we are going to attempt and reset the WordPress Admin password for the user tutor@linuxshelltips. To be sure that this user is an Admin, take note of the above ID column value 1. We are going to compare it with the user_id column values in the wp_usermeta WordPress database table.
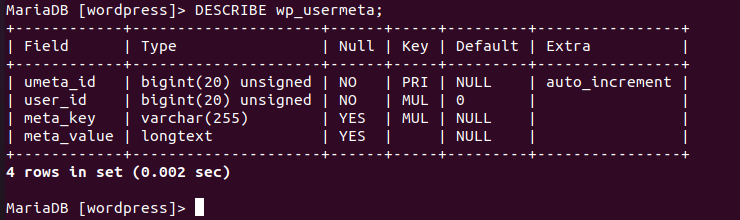
MariaDB [(none)]> DESCRIBE wp_usermeta;
MariaDB [(none)]> SELECT user_id, meta_key, meta_value FROM wp_usermeta;
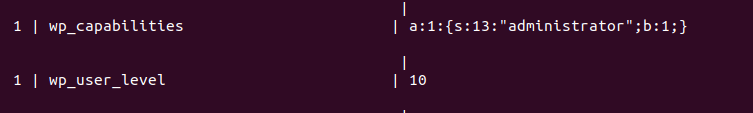
The database table wp_usermeta’s user_id output is identical to wp_users’ ID. The displayed meta_key and meta_value table column entries confirm that the user whose password we want to change is indeed an Admin user.
To change this user’s password, copy the MD5 Hash password encryption we generated earlier and apply it to the following SQL statement.
MariaDB [(none)]> UPDATE wp_users SET user_pass= "6e1fe1be8e8034a1e5fe95a1d2fec05f" WHERE ID = 1;
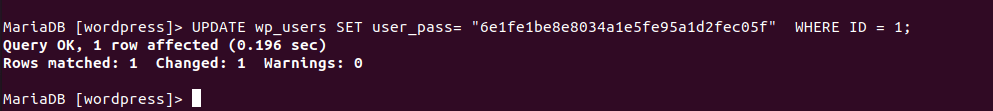
The SQL query execution was a success. The MD5 Hash encryption protects the user passwords from unnecessary leaks in case an unauthorized user manages to access the MySQL database.
Testing the New WordPress Admin Password
Now you can test your new Admin user password on the WordPress site by logging.
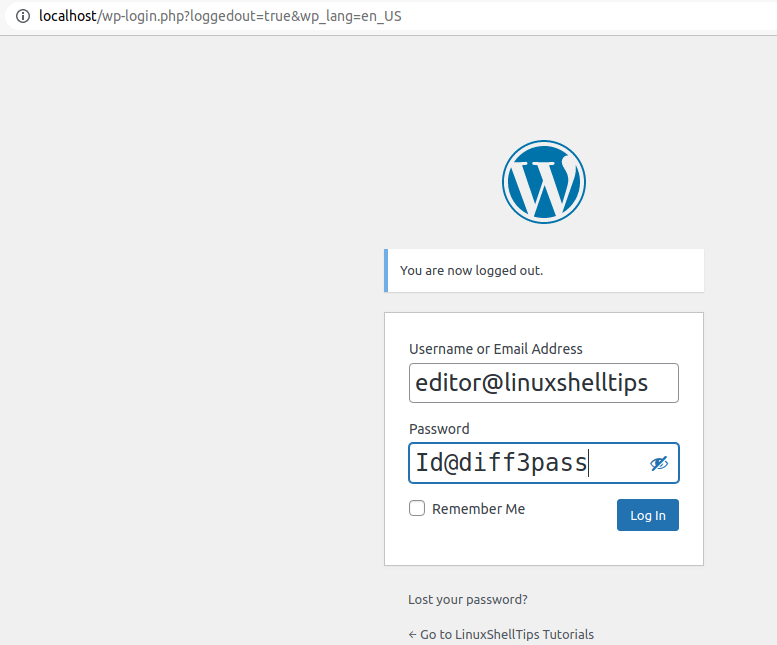
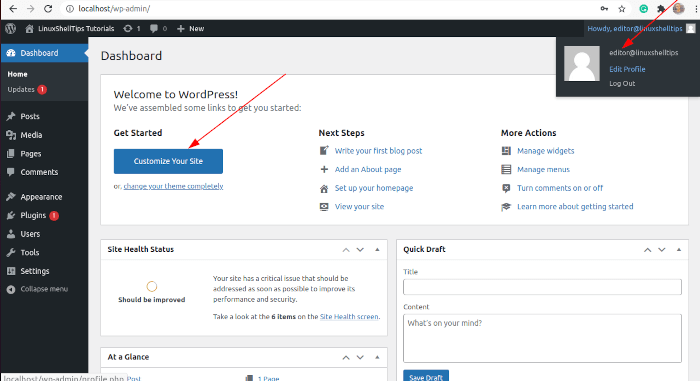
WordPress Admin password reset mechanism via the MySQL/MariaDB CLI has the advantage of re-activating a user account with forgotten credentials like user email and password. It can also help manage other WordPress user accounts facing the same predicament.
