Remote access to other operating system environments on an active network is not just a thing of the SSH (Secure Shell) protocol. Telnet achieves the same functionality through TCP/IP protocol.
With Telnet, you not only get to establish successful remote connections but also troubleshoot and test the system services that define the remote computing environment.
For instance, we could check if a particular port is active/open/listening on the targeted remote system. It is worth noting that Telnet utilizes port 23 for its remote TCP connections.
Install Telnet in Linux
This article will walk us through the installation and usage of this ancient server administration protocol. Since Telnet is unencrypted, its recommended usage is for testing purposes only and in user-defined networks.
$ sudo apt-get install telnetd [On Debian, Ubuntu and Mint] $ sudo yum install telnetd [On RHEL/CentOS/Fedora and Rocky Linux/AlmaLinux] $ sudo emerge -a net-misc/netkit-telnetd [On Gentoo Linux] $ sudo pacman -S telnetd [On Arch Linux] $ sudo zypper install telnetd [On OpenSUSE]
Check on its status to make sure it is up and running.
$ sudo systemctl status inetd
Testing Remote Linux Connections via Telnet
To perform an unencrypted connection to remote host systems via Telnet, we first need to identify the IP address of the machine we are targeting.
$ ifconfig
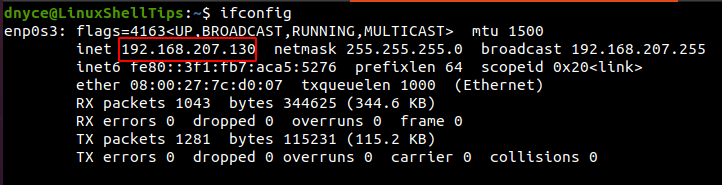
Also, the targeted remote Linux machine should have Telnet installed on it as per the suggested installation commands discussed above.
$ sudo apt install telnetd -y
Also, check on the status of Telnet to make sure it is running on the remote machine too.
$ sudo systemctl status inetd
On the Telnet-powered server machine, we will adhere to the following syntax rule:
$ telnet [remote-system-ip-address]
The implementation of the above syntax rule will look like the following:
$ telnet 192.168.207.130
The above IP address belongs to the targeted machine. If you are using or have a firewall enabled on your remote/targeted Linux machine, you will need to allow traffic through port 23 since Telnet uses it for its network communication.
$ sudo ufw allow 23/tcp [On Ubuntu & Debian] $ sudo firewall-cmd --permanent --zone=public --add-port=23/tcp [On RHEL] $ sudo firewall-cmd --reload
We can now attempt to make a Telnet connection to a targeted/remote Linux machine.
$ telnet 192.168.207.130
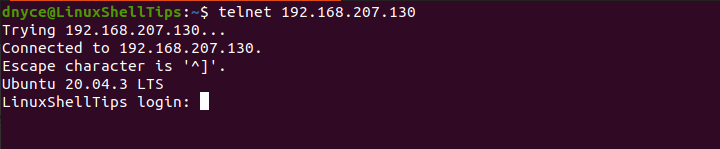
An acceptable user login input will be followed by a password request which when we key in should give us managerial access to the remote Linux system. Once granted access, the interface should change to something like the following:
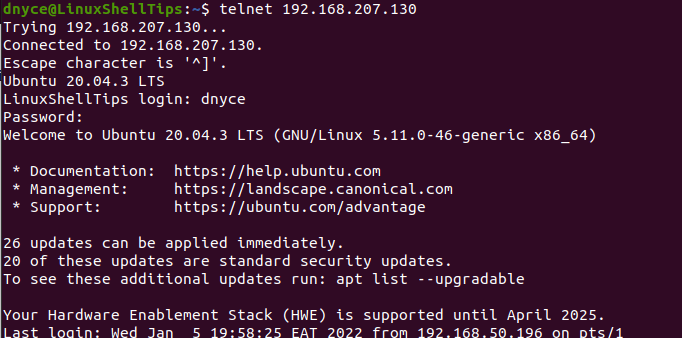
From here, we can perform normal OS operations if needed.
Testing Open Ports on Linux via Telnet
Another interesting feature Telnet offers its users is its ability to detect an open or closed port on a targeted remote system via its IP address. This feature is useful in figuring out any vulnerabilities present on your system.
For instance, we can check if the above discussed remote system has port 80 open by executing the following command:
$ telnet 192.168.207.130 80
If the port is open, you will see an output like the following:
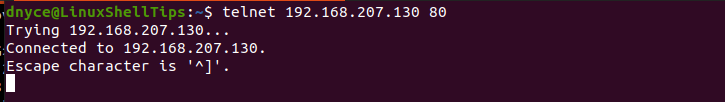
If the port is blocked, then expect the following outcome:
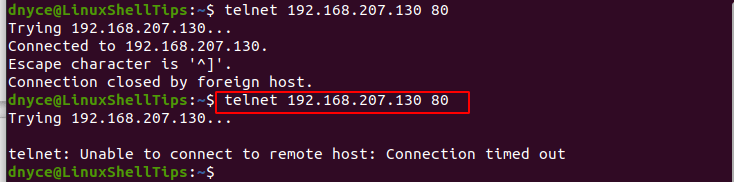
You can also test your mail server through the SMTP port 25:
$ telnet 192.168.207.130 25
With Telnet, you can make remote connections to other client computers with the same approach as SSH and additionally test any vulnerabilities on your system by troubleshooting if a suspicious port is listening/open or unintentionally closed.

You should mention how insecure telnet is and should never use it as a remote administration connection – use ssh for this. installing the telnet client as a port testing tool is fine.