Data transfer is one of the most common operations carried out by users over the internet. When transmitting data, caution needs to be taken to ensure that data is transferred securely and not compromised.
In this guide, we look at some of the secure data transfer protocols and explore the differences that exist between them.
SFTP – Secure File Transfer Protocol
SFTP, short for Secure File Transfer Protocol, SFTP is a protocol that leverages the SSH protocol to provide high-level security during file transfer.
It helps users to securely transfer files over the internet using SSH encryption. Since it runs over SSH, SFTP uses port 22 to establish a connection to a target system.
In addition to transferring files, it also allows you to perform additional operations such as listing and deleting files and directories on the remote target.
To use SFTP, you need an SFTP client and an SFTP server. The client software allows you to establish a connection to an SFTP server. You can access a remote target using either a GUI client such as FileZilla and Solar-PuTTY or on the command line.
SFTP is packet-based rather than text-based, which means that it is typically faster than other protocols since packet-based protocols are compact, and hence, easier to process. On the other hand, text-based protocols have multiple characters and so, they take longer to decrypt.
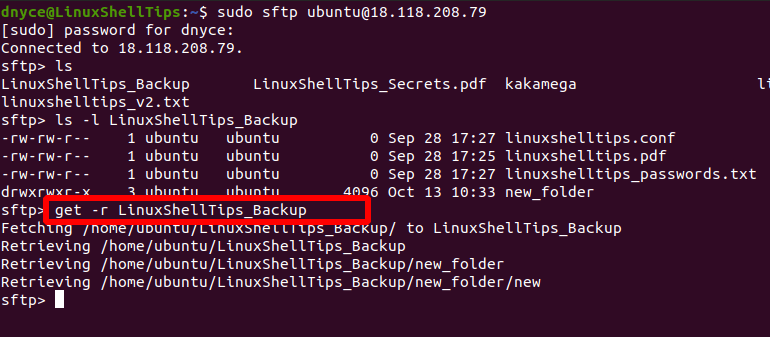
SCP – Secure Copy
Secure Copy or SCP is a network protocol that securely copies files between Linux systems over a network. The SCP protocol relies on SSH for data transfer, and therefore, requires a password or SSH key to authenticate with remote systems.
You can perform the following tasks using SCP:
- Copy files/folders from your local system to a remote target.
- Copy files/folders from the remote target to your local system.
Both SFTP and SCP use SSH and run over TCP port 22.
However, SCP is non-interactive and is only used for transferring files from one system to another. It does not perform additional tasks on the remote system such as listing or removing files and directories. It is simply a data transfer utility. SFTP is more elaborate and provides more options to manipulate files and folders on remote systems.
When it comes to speed, SCP beats SFTP hands down. It is generally faster, especially over high latency networks.
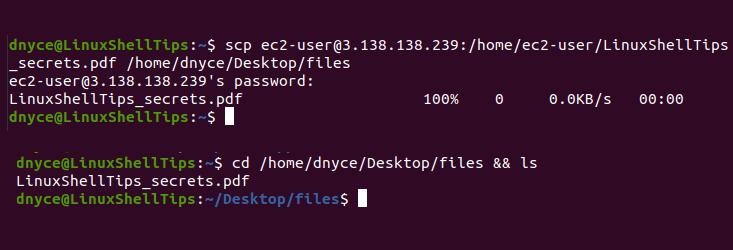
Important Notice
According to OpenSSH developers, the SCP protocol is now old and outdated. Thus, it is recommended to use more modern and safer protocols such as SFTP and Rsync as security issues are constantly being reported in connection with SCP.
In fact, one of the latest security enhancements in RHEL 9 is the deprecation of the SCP protocol in favor of SFTP. Instead of SCP, SFTP is now the default file transfer protocol and covers most of the SCP use cases.
RHEL plans to eliminate SCP in the upcoming releases of Red Hat Enterprise Linux. Instead of SCP, Rsync is a better alternative that also uses SSH for encryption.
FISH – Interactive Shell
FISH stands for Files transferred over SHell protocol, which was originally designed for the midnight commander file manager and uses the SSH protocol to establish a connection to a remote system.
A FISH protocol is supported by popular FTP clients such as FileZilla and file managers such as Krusader, Konqueror, Midnight Commander, and so on.
Though not as popular and widely used compared to SFTP and SCP, FISH still provides secure data transfer between systems. The remote system only needs to be running the SSH daemon.
That was a brief walkthrough detailing the differences between SFTP, SCP, and FISH protocols.

The URL about “fish” incorrectly points to the unfortunately similarly named “Fish shell”.
The “Fish” you mean here is the Filesystem over Ssh” which is an entirely different thing. I don’t have a good project URL for fish protocol
RedHat 9 is the deprecation of the SCP protocol. To view more details, please visit https://www.redhat.com/en/blog/openssh-scp-deprecation-rhel-9-what-you-need-know