SELinux (“Security-Enhanced Linux”) is a robust security framework within some Linux distributions like Fedora, which utilizes security contexts to enforce fine-grained access controls and protect system resources, such as files, from unauthorized access and potential threats. These security contexts are a vital concept.
Think of a security context as a digital ID for files that consists of “Labels” (like file names) and “Types” (like categories), which tell the system what they are and how they should be treated.
However, as your system becomes more complex, finding files with specific SELinux security contexts, labels, and types can become challenging. This article will explore the process of locating these files, offering clarity in this complex task.
Before delving deeper into the method of searching for files with specific SELinux security contexts, labels, and types, let’s first understand how to display the SELinux security context associated with any file.
List Files with SELinux Security Context
The ls command offers a -Z flag to display files and directories with their corresponding SELinux security contexts:
$ ls -Z
The output will display each file’s user, role, type, and level along with its name. However, each piece of information is separated by a ':' symbol.
Here is the table with possible “user“, “type“, “role” and “limits” of SELinux security contexts along with their purposes:
| Security Context Labels | Purpose |
| unconfined_u | It is the default user for unconfined domains. |
| system_u | It is the default user for system domains. |
| user_u | It is the default user for user domains. |
| object_r | It defines the object’s role within the security context. |
| system_r | It declares the system’s role within the security context. |
| user_home_t | It locates files in a user’s home directory. |
| var_log_t | It permits read and write access to system logs. |
| httpd_sys_content_t | It grants read-only access to web server content. |
| mail_spool_t | It gives access to mail spool files. |
| etc_t | It offers access to configuration files in /etc directory. |
| no_limit | It refers to no specific security context restrictions. |
So let’s try to list files in the “/var/www/” directory along with their SELinux security contexts by executing the command stated below:
$ ls -Z /var/www/
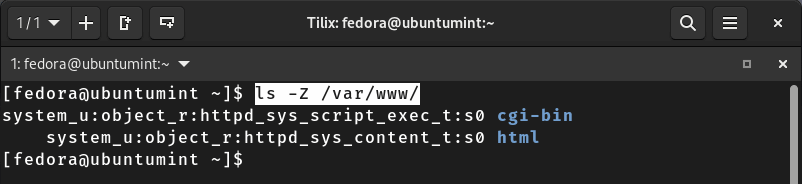
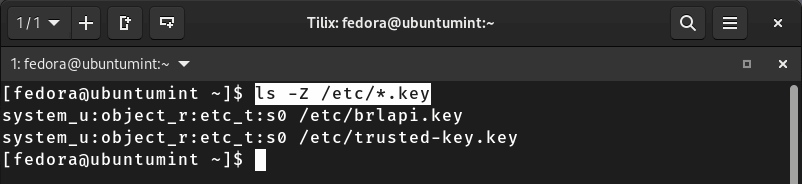
Moving forward, you can list all files with a specific extension in any directory along with their associated SELinux security contexts. For instance, by executing the command given below, you can obtain security context labels for all files with the “.key” extension in the “/etc/” directory.
$ ls -Z /etc/*.key
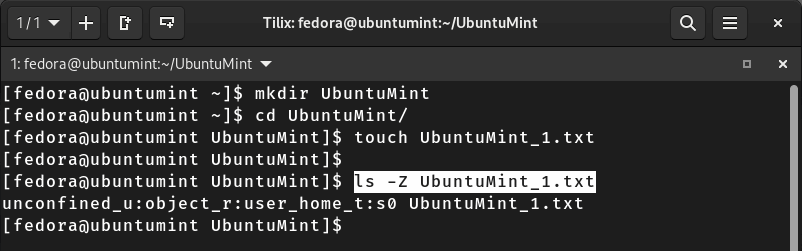
However, if you want to just display the SELinux security context label of an individual file, you can execute the “ls -Z” command with the file name as shown below:
$ ls -Z UbuntuMint_1.txt
Now that you have learned, how to display the SELinux security context label and type of any file or directory. Let’s see how to locate files that have any specific security context, labels, and types.
File Files with a Specific SELinux Security Context, Labels, and Types
The well-known find command offers an effective flag named '-context' that allows users to specify the security context label.
Find Files by SELinux Security Context Label
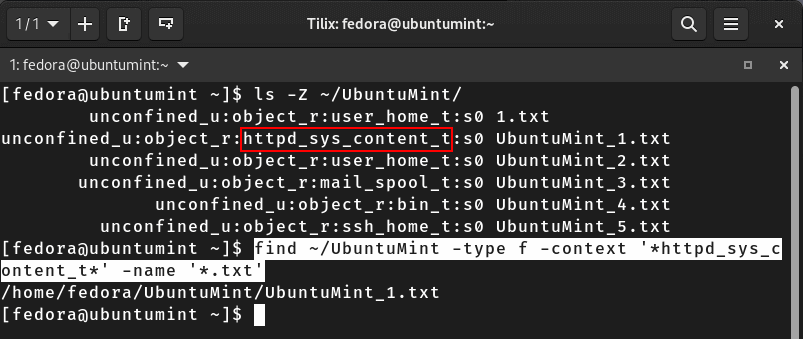
Let’s locate all the files with the “.txt” extension in the “~/UbuntuMint” directory that is linked to web server content and has the security context label “httpd_sys_content_t”.
In this label, “httpd_sys_content” identifies the type of file we’re looking for. Since we’re focusing on this particular type, let’s use the “*” wildcard character to explore all potential users, roles, and levels.
$ find ~/UbuntuMint -type f -context '*httpd_sys_content_t*' -name '*.txt'
You can even specify a role and type in the security context label and add “*” to explore all potential users and levels by executing the following command:
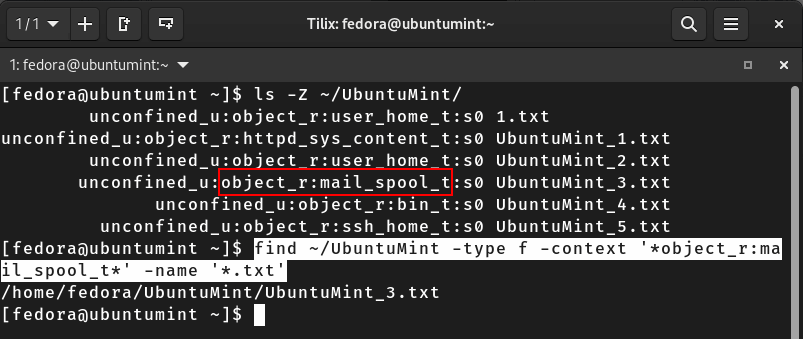
$ find ~/UbuntuMint -type f -context '*object_r:mail_spool_t*' -name '*.txt'
The above command will list all TXT files in the “UbuntuMint” directory with the “object” role and “mail_spool” type.
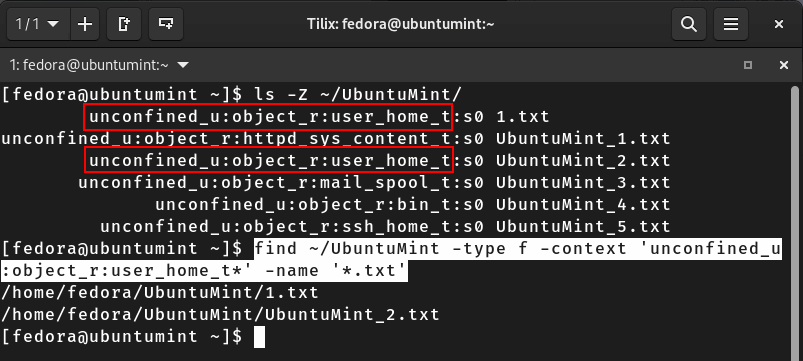
Continuing onwards, let’s obtain TXT files with a specific “user”, “role” and “type” by running the given command:
$ find ~/UbuntuMint -type f -context 'unconfined_u:object_r:user_home_t*' -name '*.txt'
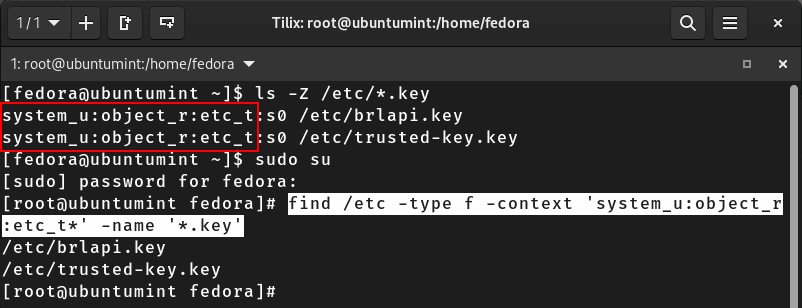
Let’s execute the command stated below to locate all files with a “.key” extension that belongs to the “system” user, has an “object” role, and is of the “etc” type in the “/etc” directory:
$ find /etc -type f -context 'system_u:object_r:etc_t*' -name '*.key'
Now that you have understood the process of searching files with a specific SELinux security context, let’s discuss another command for the same purpose.
Locate Files with a Specific SELinux Security Context, Labels, and Types
Users can combine the “ls -Z” command with the “grep” command to filter the files depending upon a specific SELinux security context.
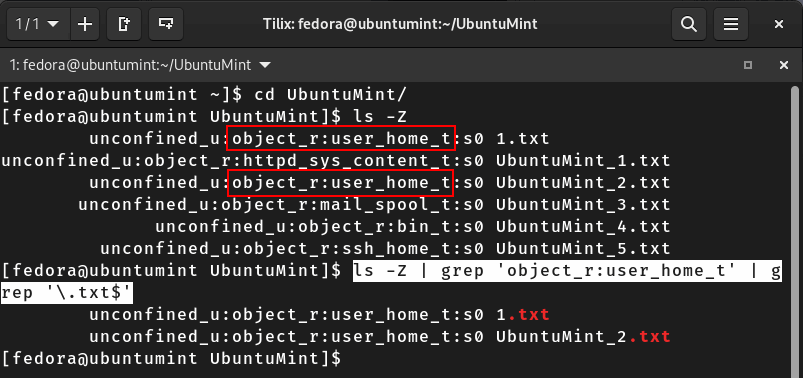
Let’s execute the following command to obtain files in the current directory along with their security context labels, filter the output using “grep” to show only the lines containing the “object_r:user_home_t” label, and finally, display only the TXT files in the terminal:
$ ls -Z $ ls -Z | grep 'object_r:user_home_t' | grep '\.txt$'
Conclusion
The SELinux uses security contexts to enforce fine-grained access controls and protect system resources, like files. The security Linux labels contain information about the user, type, role, and permissions of the files.
This guide discussed various commands for locating files with specific SELinux security contexts, labels, and types. By mastering these commands, you can enhance the security and control of your system resources.
