Welcome to the fascinating world of Metasploit in Kali Linux! If you’ve ever been curious about ethical hacking and penetration testing, Metasploit is the ultimate tool that you don’t want to miss out.
In this step-by-step guide, we’ll walk you through the process of installing Metasploit on your Kali Linux system, giving you access to a powerful arsenal of ethical hacking tools at your fingertips.
Before delving into the installation process, let’s take a moment to understand what Metasploit is.
What is Metasploit?
Metasploit is an open-source well-known framework utilized by cybersecurity personnel and ethical hackers to assess the security of systems. It allows you to simulate real-world cyber attacks, identify vulnerabilities, and strengthen your defenses against potential threats.
This powerful toolset allows you to stay one step ahead of potential threats and strengthen your defenses. From conducting penetration tests to performing vulnerability assessments, Metasploit is the go-to toolkit for those seeking to protect and reinforce their digital assets.
Prerequisites and Requirements
To install Metasploit, you need to meet certain prerequisites and requirements:
- Disable Anti-virus Software – Anti-virus software may flag the Metasploit Framework as malicious due to its ability to exploit vulnerabilities, potentially interrupting the installation process. To avoid any interruption it’s recommended to disable the Anti-virus software.
- Disable Firewalls – Firewalls may detect the Metasploit as malware and disrupt the download process. To ensure a smooth installation process, disable local firewalls before running or installing Metasploit.
- Obtain Administrator Privileges – You require administrator privileges of your Kali Linux to install the Metasploit Framework. Administrator privileges grant you the necessary authority to make changes to the system, including installing software and configuring settings.
Is Metasploit Pre-Installed in Kali Linux?
Yes, Metasploit Framework is pre-installed as part of the default software package in Kali Linux 2.0, but the pre-installed Metasploit Framework Community edition is no longer supported on Kali Linux 1.0.
Note: For more detail about Metasploit, visit the official website of Rapid7.
To confirm whether Metasploit Framework is already installed on your system or not, you can open the “msfconsole” by typing the given command in the terminal:
$ msfconsole msfconsole: command not found
The error “msfconsole: command not found” indicates that Metasploit is not installed on your system. Conversely, if it starts without any errors, means that Metasploit is already installed on the system, allowing you to update it using the appropriate installer.
Install Metasploit in Kali Linux
To install Metasploit Framework in Kali Linux you can use any of the methods mentioned below.
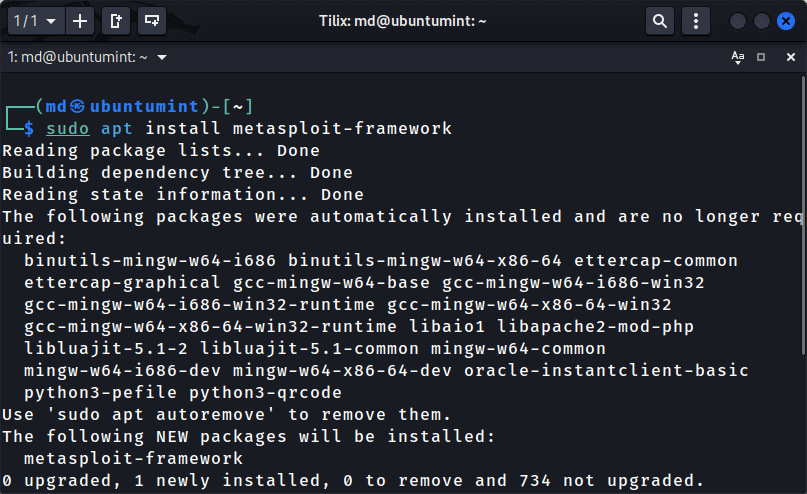
1. Install Metasploit Using Repository
First, you need to update the local package repository and then install Metasploit by running the apt commands as shown.
$ sudo apt update $ sudo apt install metasploit-framework
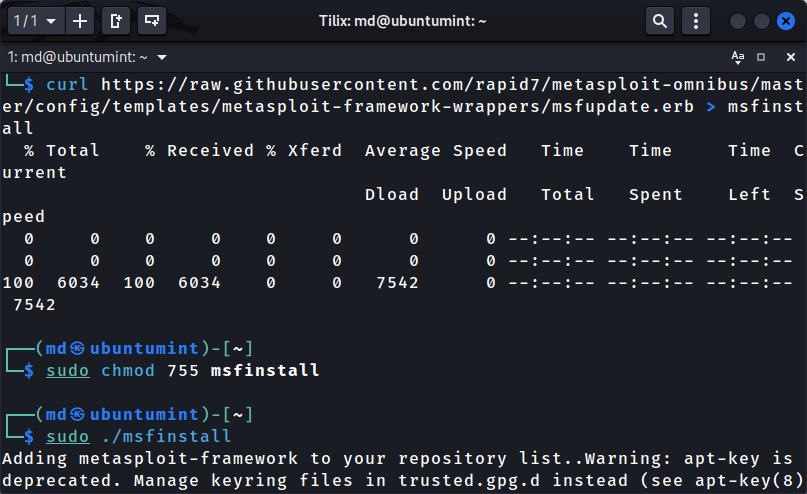
2. Install Metasploit Using msfinstall Script
Another method to install Metasploit is by utilizing the Rapid7 signing key. You can achieve this by downloading a script named “msfinstall” which will automate the process of importing and configuring the package for Metasploit installation.
The commands to download the script and install Metasploit on Linux.
$ curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall $ sudo chmod 755 msfinstall $ sudo ./msfinstall
After successfully installing Metasploit, the next step is to manage the database (PostgreSQL). However, you might be curious about why managing a database is crucial for Metasploit.
Why Is Managing a Database Important for Metasploit?
The reason is straightforward, managing the database facilitates efficient data storage, enables collaboration among multiple users, and allows for effective tracking and reporting of assessment results. It also offers effortless integration with other security tools, streamlining the penetration testing process.
The following commands are being used to manage the database for Metasploit:
| No. | Commands | Usage |
| 1. | msfdb init | Initiate the database |
| 2. | msfdb reinit | Reset the database to its initial state |
| 3. | msfdb delete | Delete/remove the database |
| 4. | msfdb start | Starts the database |
| 5. | msfdb stop | Stops the database |
| 6. | msfdb status | Shows the database status |
| 7. | msfdb run | Start the database and execute “msfconsole” |
Setup PostgreSQL for Metasploit
To start the database, simply execute the “start” command as given below:
$ sudo msfdb start [+] Starting database
After starting the database, let’s initialize it by using the “init” command, which will create a user, a database, configuration file and initialize the database schema:
$ sudo msfdb init [i] Database already started [+] Creating database user 'msf' [+] Creating databases 'msf' [+] Creating databases 'msf_test' [+] Creating configuration file '/usr/share/metasploit-framework/config/database.yml' [+] Creating initial database schema
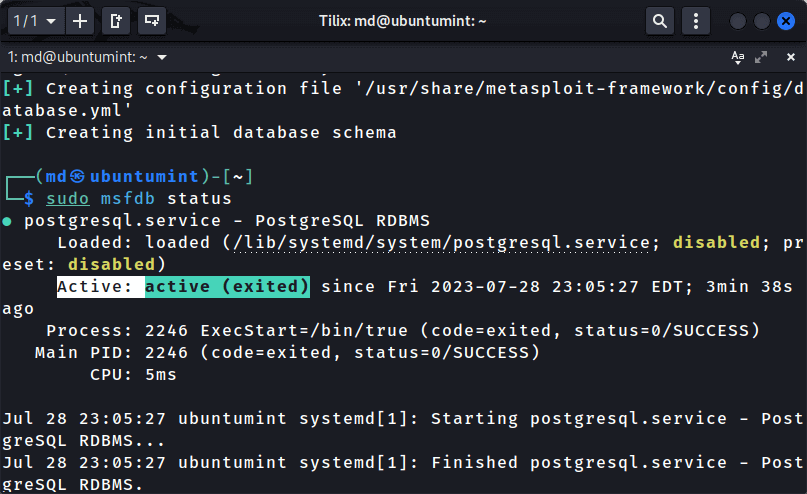
Next, check the status of the database for confirmation:
$ sudo msfdb status
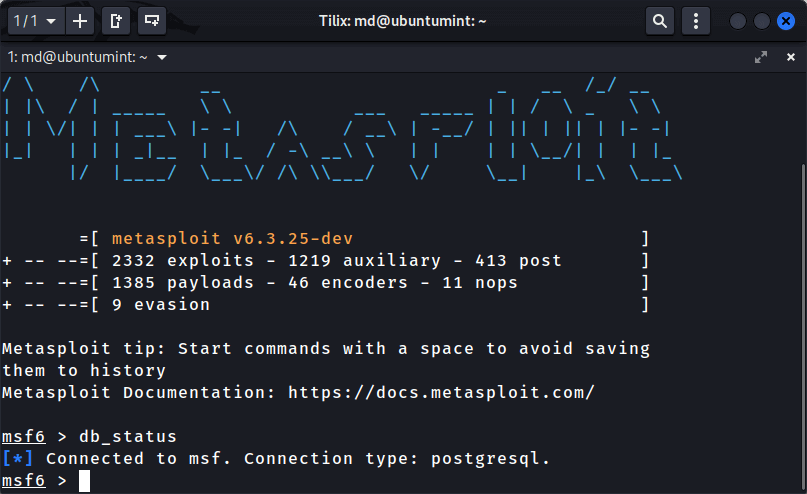
Once you have set up the database you can open the Metasploit framework by executing the given command:
$ msfconsole
This command may take some to start:
[*] Starting the Metasploit Framework console...
When the Metasploit starts, you can confirm if the database is connected or not by checking the status. To do that simply type the given below command in the Metasploit terminal:
msf6 > db_status [*] Connected to msf. Connection type: postgresql.
and the message “Connected to msf” indicates that the database has been connected.
If the database is not connected to the Metasploit, you can connect it by using the given below syntax:
msf6 > db_connect your_msfdb_user:[email protected]:5432/msf_database
From the above syntax you need to replace:
- “your_msfdb_user” with your database user name.
- “your_msfdb_pswd” with your database password.
Once everything is set up you can enjoy the power of Metasploit!
Conclusion
Metasploit is a powerful open-source penetration testing framework developed by Rapid7 which aids in assessing system security, identifying vulnerabilities, and strengthening defenses against potential threats.
By following the step-by-step guide, users can easily install Metasploit and manage the database to unleash the full potential of this essential toolkit, protecting and fortifying their digital assets effectively.

Thanks so much for sharing. It was very helpful.