WordPress continuous and growing worldwide popularity has made it the go-to content management system. It is now the center of the universe for all individuals that want to create, edit, and publish their contemplated ideas. However, all the attention that WordPress has brought on itself comes at a price. Malicious web traffics are always trying, and on some occasions, manage to bring down targeted WordPress sites.
Such attacks can have dire effects on the health of a running website and even render the MySQL service unresponsive because of depleted system resources. Under such circumstances, a WordPress administrator cannot escape from erroneous messages like Out of Memory and Error connecting to the database. Such error messages are related to XML-RPC attacks and this article guide is going to show us how to deal with them.
[ You might also like: How to Block Access to wp-admin and wp-login in Nginx/Apache ]
Understanding XML-RPC
The XML-RPC protocol helps WordPress achieve the execution of certain remote functions. It manages this role through the initiation of a direct communication channel with other externally configured systems. This communication entails data transfer over the HTTP protocol with XML being the preferred encoding mechanism.
A perfect case example is using your smartphone gadget to post or publish on your WordPress site. The latter action is possible through an enabled xmlrpc.php remote access feature.
The following traits classify any WordPress site user, owner, or administrator as a victim of XML-RPC attacks.
- Web server logs with “POST /xmlrpc.php HTTP/1.0” or similar entries.
- A WordPress site that is down broadcasting “Error connecting to database”.
Recognizing an Active XML-RPC Attack
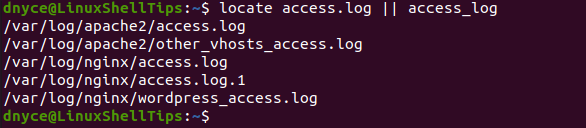
The web server log files on your Linux system distribution should be searched for the viability of XML-RPC attacks. You can use the following locate command.
$ locate access.log || access_log
For example, to check on the Nginx access log for the possibility of an XML-RPC attack, we would use the grep command:
$ grep xmlrpc /var/log/nginx/access.log
If the access.log file output from the execution of the above command has the string:
“POST /xmlrpc.php HTTP/1.0”
It will be a positive test for an active XML-RPC attack.
How to Block the Execution of XML-RPC Attacks
The security concerns associated with the usage of XML-RPC are slowly taking the feature to a deprecated state. With a new WordPress API taking over, the popularity of XML-RPC is sinking continuously, hence the need to have it blocked from your WordPress site.
Disable XML-RPC via WordPress Plugin
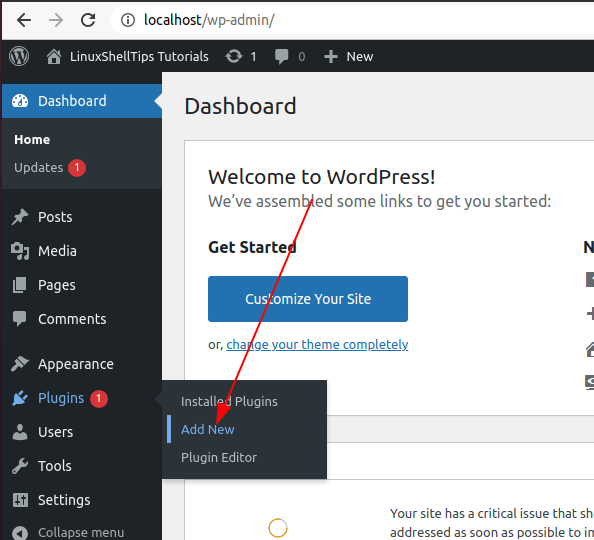
Visit the plugin section of your WordPress Admin page and click on the ‘Add New‘ button.
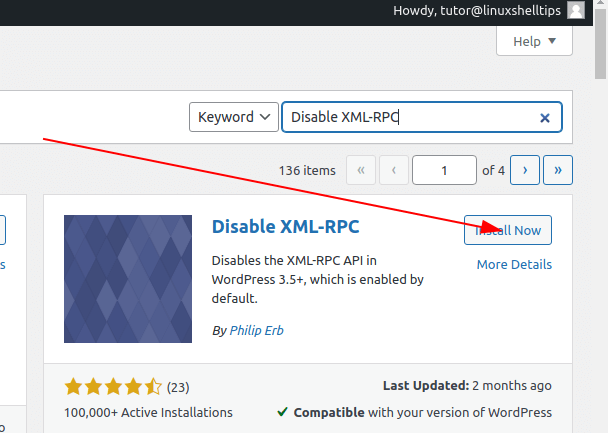
Search for plugin “Disable XML-RPC” and install it.
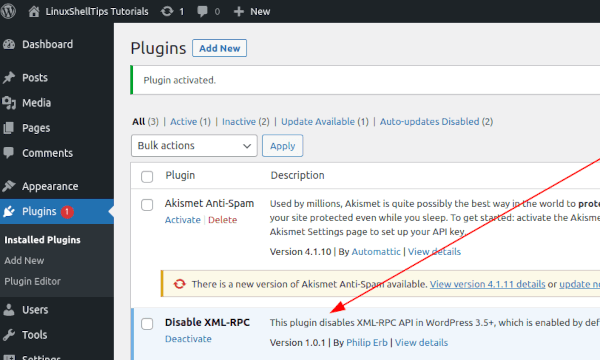
Install, activate, and enable auto-updates on the plugin.
Block XML-RPC Access via Nginx
If you are the sort of WordPress website administrator that believes in manually fixing all active and site-related technicalities, then this solution is for you. The first step is to trace the webserver configuration file associated with your WordPress site.
For Nginx, it would be a configuration resembling the following file.
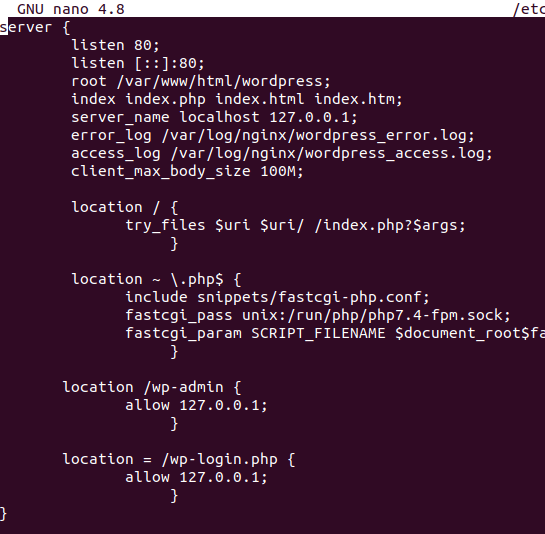
To block XML-RPC access in Nginx, add the following line:
location = /xmlrpc.php {
deny all;
}
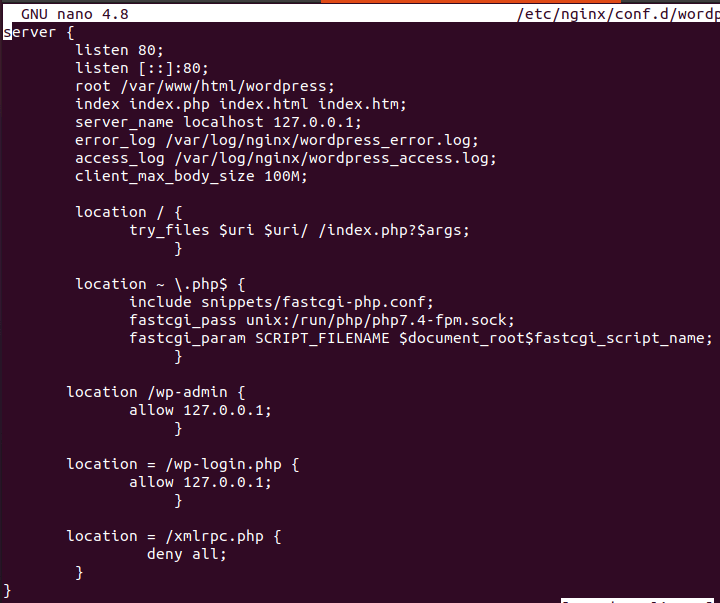
Save the file and restart Nginx.
$ sudo systemctl restart nginx
Block XML-RPC Access via Apache
For Apache, it would be a configuration resembling the following file.
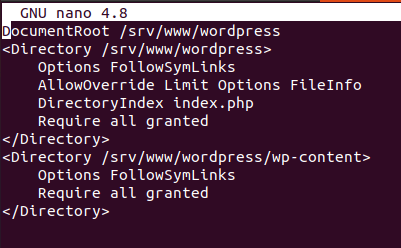
To block XML-RPC access in Apache, add the following line:
<Files xmlrpc.php> Order Deny,Allow Deny from all </Files>
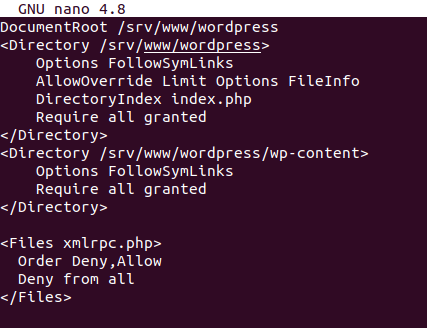
Save the file and restart Apache.
$ sudo systemctl restart apache2 OR $ sudo systemctl restart httpd
Disable WordPress XML-RPC via .htaccess
You can also block access to xmlrpc.php using the .htaccess file, simply copy and paste the following code in your .htaccess file:
<Files xmlrpc.php> order deny,allow deny from all </Files>
Blocking this soon-to-be deprecated if not already deprecated XML-RPC feature from your WordPress site is a resource-saving move. If your WordPress platform uses too many resources, it will tend to go offline. Blocking this feature saves you from being another victim of WordPress XML-RPC brute force attacks.

About the code snippet in the config file – Why add an Nginx location directive in wp-config.php?