As you might already know, SSH (Secure Shell) is a network protocol for securely accessing a computer remotely. The server and client software in Linux are thereby known as SSH Server and SSH Client respectively and have many implementations.
By default, SSH allows you to log in to any user of the computer, as long as you have the password for the user. However, this comes with the same problem which is faced by any software using password-based authentication: an invitation for an attacker to exploit and gain admin access.
Today, we will see how to disable SSH login to a specific user, and more importantly, to the root user.
Disable SSH Access to User
You can log in to a system using SSH with any user, using the following syntax:
$ ssh tempuser@localhost
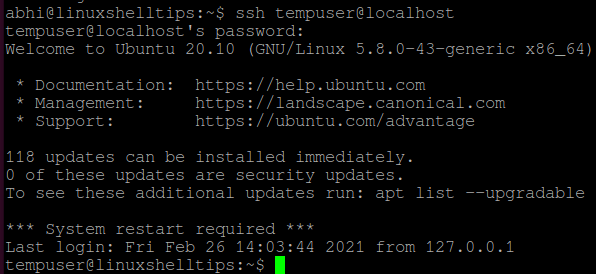
Right now, SSH access is allowed on my machine for all users. Let us now deny access to a particular user called ‘tempuser‘.
Open file ‘/etc/ssh/sshd_config’ in any text editor.
$ sudo vim /etc/ssh/sshd_config
Add the following line at the end of the file:
DenyUsers tempuser
Important: There is a ‘Tab‘ between ‘DenyUsers‘ and ‘tempuser‘ and not space. It won’t recognize the directive if you add a space.
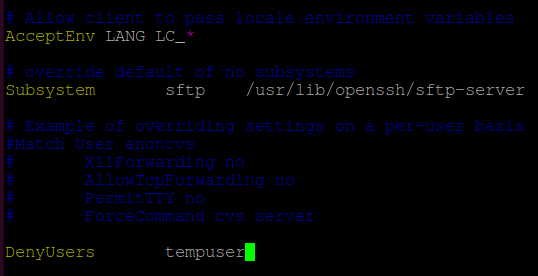
Save and exit the file.
Restart SSH server with the following command:
$ sudo systemctl restart sshd
If you are using a system that does not have SystemD, run:
$ sudo service sshd restart
Now, try logging in to localhost with user ‘tempuser’ using SSH. It should show the error ‘Permission denied’, as displayed below:
$ ssh tempuser@localhost
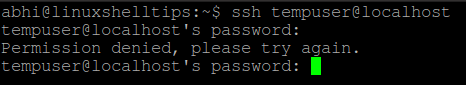
Disable SSH Root Access
The same way described above can be used to disable login to a root user. However to disable complete root access, i.e., to disable access to all root users, follow the steps given below.
Open the file ‘/etc/ssh/sshd_config’ in any text editor and search for the string ‘PermitRootLogin’. Uncomment the line and if it has any other value, set the value to ‘no’.
PermitRootLogin no
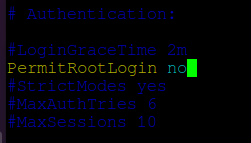
Save and exit the file. Restart SSH with:
$ sudo systemctl restart sshd
Or if you are not having SystemD:
$ sudo service sshd restart
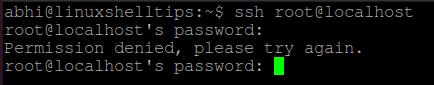
Now try logging in to localhost with user ‘root’. It will also show the error ‘Permission Denied’.
$ ssh root@localhost
Conclusion
In this article, we learned how to disable SSH login access to a specific user. Restricting access to a Non-root user depends on individual scenarios, however, access to Root must be always restricted.
If there is a need for remote Root access, you should set up SSH with RSA authentication, which is more secure than password authentication. Read the man page of SSH (‘man ssh’) for more details.
Thanks for reading and let us know your thoughts in the comments section below!

At least on Fedora 28, this is what I get with ssh.
So it seems at least on some systems `restart sshd` is required
rather then
It’s the same, sshd.service is just an alias to ssh.service.
Also, a tab after DenyUsers is not necessary or important, space works just fine.